
Unveiling the Secrets Behind Successful Credit Carding Strategies. With How to find who is Invisible on Yahoo messenger ?
Credit carding is a big topic online today. This guide is here to show you the secrets of making it work, legally and ethically. By learning about online carding methods, setting up strong defenses, and keeping up with security changes, you’ll know how to stay safe.
Key Takeaways
- Explore the legality and consequences of credit carding activities
- Understand the popular platforms and tools used in the carding community
- Learn how to build a reliable carding infrastructure and source valid credit card information
- Discover strategies to avoid common pitfalls and scams in the carding industry
- Understand the importance of cryptocurrency and anonymity in carding transactions
Introduction to Credit Carding and its Risks

In the digital age, more people are trying credit carding for quick money. Credit carding means using credit card info without permission. This can range from buying things with a stolen card to complex scam activities. Even if some ways of using stolen card info are legal, most are not.
Understanding the Legality and Consequences
The rules and outcomes of credit carding are complex and depend on the situation. Using stolen card info for buying things illegally is a crime. It can lead to big fines and possibly jail time. Sometimes, what's legal in credit carding isn't clear, which is important to know to stay out of trouble.
Places like fe acc18 and fe acc18 ru login now exist to sell stolen card info. They're known as online credit card shops. These sites let cybercriminals trade stolen card info, which includes names, CVV Dumps codes, and how much money is left on the card. While these sites offer privacy, the dangers and legal issues shouldn't be ignored.
Deciding to get involved in credit carding means understanding the risks and thinking about the ethics. It's crucial to learn about the dangers and keep up with the latest information. This way, you can make smart choices and steer clear of the problems linked to this risky and often illegal activity.
"Carding is on the rise in the digital age, with many viewing it as an easy way to make quick money."
fe acc18, fe acc18 ru login, credit carding, feshop, feccshop, fe ccshop

In the world of credit card activities, certain terms are key, like "fe acc18 ru login" or "feshop." These words point to different online places and tools. They're used by people into credit card things.
The "fe acc18" platform helps over 47,316 users with their credit card needs. It offers many types of cards. The "FE CCShop" aids over 45,288 people with smooth transactions. They both bring options to a big group, from "LIVE CC" to "DUMP + ATM PIN."
Other platforms include "feshop," "feccshop," and "fe ccshop." They attract people interested in credit cards online. The "fe shop 18 ru" in Russia has over 100,000 credit and debit cards from everywhere. This makes it a top spot for carding resources.
It's important to know what these credit carding terms mean. This understanding helps in the credit carding world. Readers can spot risks, finds opportunities, and resources by knowing this.
"The FE ACC18 platform makes FE CCShop deals safe. It gives customers a trusted place for their credit card use."
Mastering Online Carding Techniques
In today's world, learning how to card online is key. With lots of online places to explore and the latest tech, the field of credit carding is always changing. The skills needed for online credit card fraud are getting more complex and advanced.
Exploring Popular Tools and Resources
The carding world has lots of sites that help in shady money activities. Platforms like fe acc18 and feshop are hotspots for finding stolen credit card info. You can buy cards like Visa Signature® or Visa® Credit Builder there.
At these sites, you can also buy and sell stolen credit card info. This info is often gotten through bad ways like phishing or hacking. People then use special software to make fake credit cards and use them for bad stuff, like buying things without permission.
Using these sites lets people stay hidden while doing bad things. But, it's risky because what they're doing is against the law and can get them in deep trouble.
"The world of carding has become increasingly complex, with a myriad of online tools and resources at the disposal of those who seek to engage in credit card fraud. While the allure of easy money may be tempting, it's crucial to understand the grave legal and ethical implications of these actions."
There’s a big market for stolen credit cards because people want them. Sites like fe ccshop and fe-ccshop are there to meet the need. They offer lots of credit card types and some can even skip the usual security checks, giving buyers a way to hide their tracks.
Still, it's easy to run into trouble on these sites. Scams are common, like selling fake info or trying to trick people with phishing. Staying careful and doing your homework is a must in the risky world of online carding.
Learning about how to card online is a big deal today. It might seem like a fast way to make money. Yet, it’s important to think about the risks and look for ways to make a living that are right and fair.
Building a Robust Carding Infrastructure
Creating a strong and secure base is key for credit carding to be successful. To do this, focus on staying anonymous, avoiding detection, and using security measures. Let's explore how to set up a reliable carding system.
Leveraging Virtual Private Networks (VPNs)
A reliable Virtual Private Network (VPN) is a must-have tool. VPNs secure your online activities and hide your IP address. This way, you can hide where you are and lower the risk of someone finding your true identity.
Utilizing Proxy Networks
Proxy networks act as a shield between your device and the web. They increase your privacy by sending your internet traffic through different proxy servers. This confuses anyone trying to track what you're doing. Fe acc18 and fe acc18 ru login can offer you access to these networks for carding.
Securing Your Devices
It's critical to keep your devices safe in the carding world. Use anti-virus programs, firewalls, and keep your operating systems updated. For chatting with your carding group, use apps like Signal or Telegram for added security.
Maintaining Operational Security
Operational security (OPSEC) is vital for your carding operations. It means using throwaway emails and being careful with data. Also, don't use your personal devices or accounts for anything related to your activities. Feshop, feccshop, and fe ccshop offer advice on OPSEC.
By using VPNs, proxy networks, securing your devices, and maintaining good security habits, you can improve your carding setup. Remember, protecting yourself in the online world is an ongoing effort that needs you to be alert, adaptable, and understand how the threats around you evolve.
Sourcing Valid Credit Card Information
In credit carding, finding good credit card details is key. It can be hard to find the right sellers. But, with the correct steps, you can lower risks and up your success chances.
Evaluating Reliable Vendors and Marketplaces
It's crucial to trust possible sellers and places to get credit card info. To do this, you need to check a few important things:
- Consider the reputation of places like fe acc18, fe acc18 ru login, and others in the carding world. By looking at what others say, you'll see if they're trustworthy and provide good information.
- Look for strong security on websites. This means they use secure domains and SSL certificates to keep your info safe.
- Look at what they offer in terms of credit card info. Good variety and quality now can lead to meeting your specific needs later.
By checking these points, you can pick better and reduce the dangers of using bad credit card info.
"Beware of places like fe acc18 and fe-ccshop for credit carding. It can get you in serious legal trouble due to its often illegal nature."
Getting the right credit card details is important for credit carding. But, it's equally vital to know the legal risks your actions might have. Platforms including fe acc18 and fe-ccshop can be dangerous due to the possible illegal nature of their activities.
Avoiding Common Pitfalls and Scams
Understanding the risks in the world of credit carding is crucial. While it may seem rewarding, the dangers are great. This includes dealing with fake sellers and the threat of being caught by the law.
Scams are a major issue in credit card fraud. Sites like fe acc18, fe acc18 ru login, feshop, feccshop, and fe ccshop often sell stolen credit card info. This info is sometimes fake, leading to risks and empty wallets.
Using non-VBV (Verified by Visa) credit card bins can also lead to bigger problems. Although they let you shop online easier, they're risky. They can help frauds avoid security checks but might also get them caught.
- Beware of fraudulent vendors and marketplace operators who may sell fake or dead credit card information.
- Conduct thorough research on sellers before making purchases on sites like fe ccshop to avoid falling victim to scams.
- Use of non-VBV credit card bins can facilitate credit card fraud, but also heightens the risk of getting caught.
- Engage in carding activities with extreme caution, as it is an illegal activity with significant legal risks and consequences.
When diving into carding, keep your wits about you. Knowing the risks and being careful can keep you safe. Stay sharp to avoid the pitfalls that countless others have faced.
"The carding world is a minefield of deception and danger. Proceed with the utmost caution, lest you fall victim to the very schemes you seek to exploit."
Managing Cryptocurrency for Carding Transactions
Cryptocurrency is now a key player in the world of credit carding. It offers a way to make transactions that are both secret and safe. Criminals are using digital currencies like Bitcoin and Monero more and more to avoid the weaknesses of the usual financial systems.
Ensuring Anonymity and Security
Unlike regular ways of paying, cryptocurrency keeps user details safe and hidden. This makes it perfect for people doing credit card fraud and other illegal acts. By using the special tech behind blockchain, people can hide who they are and keep their money routes secret.
Now, places like fe acc18, fe acc18 ru login, feshop, feccshop, and fe ccshop are really popular for carders to handle their cryptocurrency deals. They not only give fresh credit card info but also work well with apps for managing digital money.
To stay safe and secret, those into carding have to be smart about crypto. They should pick coins that focus on keeping things private. Using tech that mixes up transactions is also a good idea. Plus, following strict rules and hiding their tracks can keep them away from people who watch out for crime.
| Platform | Monthly Active Users | Key Features |
|---|---|---|
| fe acc18 | 800,000 | Diverse selection of compromised credit card information, user-friendly interface, emphasis on security and anonymity |
| feccshop | 47,000 | Offers virtual credit cards in addition to dumps, strong focus on providing the latest credit card data |
| feshop | 800,000 | Extensive database of over 15 million records, wide range of credit card details and services, trusted by the carding community |
Learning how to manage cryptocurrency is key to staying out of trouble. It helps avoid problems with the law, big fines, and a bad name. As carding methods change, knowing how to use digital money securely and without being seen is crucial.
"Staying anonymous is a key benefit on platforms like Fe CCShop to avoid getting caught by law enforcement."
Leveraging Botnets and Proxy Networks
In credit carding, advanced users know how to hide with botnets and proxy networks. These tools are key in hiding where fake transactions come from. They keep people who break the law safe from being caught by the police and other security measures.
Botnets are basically groups of computers controlled by someone bad. They give those who do carding a flexible way to carry out their plans. This happens by using the infected computers' power and internet to hide who they really are. They can do bad things without it looking like it's coming from them. This trick is even better with proxy networks. They make internet traffic go through different servers. It then becomes very hard to find out where everything's really starting from.
These tools make a tangled mess that's hard to untangle. It's tough for the police to find where the bad action began. Also, the big size and how scattered botnets are can beat the security set up to protect against them. This lets the bad actors get away with their crimes without being caught easily.
But, using botnets and proxy networks in credit carding is not just a technical issue. It's also a big problem for the law and what we think is right. Even though some use these tools for good, more people are noticing the bad. They are calling for stronger laws and to use good technology to fight against these criminal actions.
The world of carding is always changing. It gets harder for the police and security people to keep up. To fight against credit carding, we need a mix of new technology and laws. But we also need to know why and how those who do carding are using their tools.
In the fight against using botnets and proxy networks for stealing, we must work together. People from all industries and countries need to work as a team. This way, we can better protect money and trust.
Exploiting Vulnerabilities in E-Commerce Platforms
E-commerce platforms are big targets for those who try to get into systems and steal credit card info. The many transactions online make it tempting for these people to try and break through the security.
Experts who steal credit card info often look for ways the platform is weak. They might find issues in the software, security steps, or ways the system checks who you are.
Some bad actors use tools like fe acc18 and fe acc18 ru login to find and test these weak spots. These tools can look for already known problems or find new ones that weren't noticed before.
After finding a weak spot, they will use different methods to be sneaky about it. They might use feshop and feccshop or fe ccshop tricks to get at customer info and money without permission.
When businesses are hit by these attacks, everyone can suffer. They might lose data, money, and their customers' trust. This is why it's so important for companies to be really careful about their online security.
Businesses must always check and improve their security to beat the bad guys. They should use tools like Address Verification System (AVS), IP Geolocation Check, and Card Verification Value (CVV) to lower the risk of fraud.
Being alert and fixing problems helps e-commerce sites keep their customers' info safe. This trust is really important for the digital world to keep growing and doing well.
Cybersecurity Measures for Carding Operations
Credit carding can bring in money, but it's risky, especially for cybersecurity. This part will look at key cybersecurity steps for safe carding. This includes using encryption, secure ways to talk, and other tools to stay safe.
Keeping credit card and personal details safe is a top issue in carding. It's key to make sure things like emails, instant messages, and file transfers are scrambled. This stops bad guys from getting in. Tools like fe acc18 and fe acc18 ru login make it safer to access places like feshop, feccshop, and fe ccshop.
Strong anti-virus and anti-malware tools are a must to stop online threats. Regular updates are needed to avoid data leaks and identity theft. Keeping these tools sharp helps protect carding work.
- Use virtual private networks (VPNs) and proxy servers to hide your IP and stay private.
- Choose strong, different passwords for each account and change them often to keep hackers out.
- Watch out for phishers and scammers who try to get your info.
- Keep an eye on your carding for any shady transactions or hacks.
Having a tough cybersecurity plan is vital for lasting carding success. These steps help reduce financial and legal dangers. They also protect your info and cash.
"Cybersecurity is the backbone of any successful carding operation. Overlooking these critical safeguards can expose you to significant legal and financial risks."
Establishing a Solid Exit Strategy
Getting into credit carding can be risky. While you might see benefits at first, the dangers and risks are high. It's important to have a strong plan to quit. This will protect you and your future.
Minimizing Risks and Potential Consequences
Even if you're doing well with credit carding, the risks are sizable. To leave safely, think about these steps:
- Gradual Withdrawal: Avoid getting too deep into credit carding. Slowly reduce what you're doing. This way, you'll lower your risks and the impact if things go wrong.
- Asset Diversification: Put your money into several places. This can be other businesses or legal jobs. It makes you less dependent on illegal money.
- Legal Counsel: Talk with a lawyer. They can help you figure out the best move legally. This might involve making a deal with the authorities.
- Financial Planning: Get advice from a financial expert. They will help you plan out your money for a legal future. This includes managing your debts and taxes.
- Personal Security: Protect your personal details and stay safe online. Good online security and a low profile will reduce your chance of getting caught.
With a smart exit strategy, you can limit the dangers of credit carding. It's all about planning ahead.
"The true measure of a person is not found in the mistakes they have made, but in the way they have responded to them." - Unknown
Quitting credit carding is hard. But, it's necessary for a secure future. With hard work, focus, and the right advice, you can make it through. This way, you protect yourself and find new chances.
Real-World Case Studies and Cautionary Tales
The credit carding world features slim margins between success and failure. We'll explore real cases and warnings to show the risks and impacts of credit card fraud.
Platforms like fe acc18 and fe ccshop were key to this illegal trade. They offered stolen card info and aided in illegal purchases. However, their popularity caught the eyes of the law. This led to their shutdown and the arrest of those behind them.
fe acc18's story warns of the dangers in this world. It shows how easy gains can quickly turn into legal issues. This story emphasizes the need for an escape plan for criminals in this trade.
"The credit carding industry is a rising form of cybercrime, showing significant growth in popularity. Platforms like fe acc18 and fe-ccshop have become hubs for the sale and purchase of compromised credit card information, fueling a thriving underground economy."
Many carders also fall prey to scams and legal traps. Their stories remind us of the dangers in this illicit trade. To stay safe, planners must act with caution and know the law well.
Studying these cases gives key insights into the credit carding world's dangers. This knowledge can help others make wise choices and avoid serious risks.
As the credit carding sector grows, so do the risks. For those thinking about illegal trading, remember the severe costs. It's crucial to think carefully before joining this risky business.
The Future of Carding and Emerging Trends
The digital world is always changing, and so is credit carding. The future will see better security, new ways to pay, and how people use these tools. These changes will affect those who try to use cards in wrong ways.
Security is getting stronger against fraud. This means it's harder to hack into card systems. Things like your fingerprint or face may soon become your main key to buy online. This should stop many card hackers from getting through.
New ways to pay, like with your phone or digital money, are growing fast. Card hackers will have to find new ways around these. They must dodge the new security on these payment types.
People doing card hacking will look for new tricks and tools to beat the changes. They will use places like fe acc18 and fe ccshop. These online shops will likely get better and offer more ways to cheat.
Even with all this, credit carding will keep moving and changing. Those trying to hack will learn new ways. They can still find success by keeping up with tech changes.
Staying sharp and secure is key for everyone in the credit carding world. By knowing and using the latest security trends, we can keep our digital world safe. This will help lower the risks of credit carding theft.
"The future of credit carding is a complex and ever-changing landscape, where the battle between security measures and the ingenuity of carding practitioners will continue to unfold."
Conclusion
The world of credit carding is complex and has many risks. We talked about fe acc18, fe acc18 ru login, and feshop methods. We also discussed how to deal with feccshop and fe ccshop. You now know the tools and strategies used in this area.
Getting quick money through credit carding may sound good. But, it's important to know the bad legal and moral effects. This guide highlighted the need for smart money choices. It also warned against using shady credit card info online.
The world of credit carding keeps changing. It's important to keep up, be watchful, and choose wisely. By making smart decisions, you can handle this area well. Remember, it’s up to you. Think carefully and stick to doing what’s right.
If you search real cc, cvv and dump, You can try it: credit carding
FAQ
What is credit carding and what are the legal and ethical considerations?
Credit carding is when someone illegally uses credit card details. Legal activities like buying stuff correctly are exceptions. But, taking and using these details without permission is a crime. It has big legal risks and punishments.
What are the key terms and concepts associated with credit carding?
In the credit carding world, you'll hear terms like "fe acc18" and others. It's very important to know these words to manage in this tricky area.
How can I master online carding techniques?
This part looks into how experts in carding go about it. You'll learn about common tools and places online where this happens. But remember, a lot of these activities are illegal. So, be careful and learn about the legal risks involved.
What are the key components required to build a robust carding infrastructure?
For successful credit carding, you need a strong setup. This involves using VPNs, proxy networks, and other tools to stay hidden and avoid getting caught.
How can I obtain valid credit card information for carding activities?
Here, you'll find ways to get credit card data. It covers checking vendors and markets to make sure the data is not stolen. Always be careful and avoid sketchy sources.
What are the common pitfalls and scams to avoid in the world of credit carding?
A lot of risks, scams, and even legal traps are out there in carding. Knowing these dangers can help you move more wisely. It helps to avoid scam artists and traps set by the police.
How can I manage cryptocurrency-based transactions for carding activities?
Cryptocurrency is now a big part of credit card operations. It offers transacting securely and privately. You'll learn here how to handle crypto in a way that's safe and keeps your financial dealings secure.
How can I leverage botnets and proxy networks for credit carding?
Botnets and proxies are vital in hiding the source of illegal actions and staying unseen. This part teaches the legal use of these technologies. But be mindful of the possible legal and moral issues they bring.
How can I exploit vulnerabilities in e-commerce platforms for carding activities?
E-commerce sites can be open doors for carding experts to reach valuable financial data. This talks about the methods to find these weaknesses and how important it is for businesses and users to have strong security.
What cybersecurity measures should I consider for my carding operations?
Carding can be profitable, but it's full of cybersecurity threats. Knowing how to protect your activities is key. It looks at using encryption, safe ways to communicate, and other defenses.
How can I establish a solid exit strategy for my carding activities?
Being in carding means facing many risks and consequences. A good exit plan is crucial to leave without legal or financial harm. It's all about reducing the dangers involved in these operations.
What real-world case studies and cautionary tales can I learn from?
Studying past carding operations can offer great lessons. You can get insights into the risks and the effects of these actions. This knowledge can guide your choices.
What are the future trends and developments in the world of credit carding?
The field of credit carding will change as technology progresses. This part discusses the future of security, new payment types, and how carding experts will adapt. It's about being ready for what's next in this industry.
How to find who is Invisible on Yahoo messenger ?
Sometimes some of your friends who appear offline in yahoo messenger may not be actually offline, they may in the ‘Invisible’ mode. This maybe if they are trying to ignore you or are too busy to talk to anyone.
There is this small trick that you can use to find out what the truth is.
Firstly open your yahoo messenger main window and double click on the name of the person whom you want to check. The chat window will open obviously.
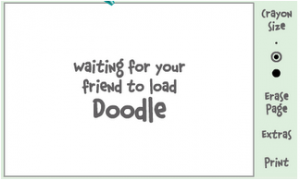
Click IMVironment button, select See all IMVironments, select Yahoo! Tools or Interactive Fun, and click on Doodle.
After loading the Doodle imvironment there can be two possibilities
1.If the user is offline Doodle are will show this “waiting for your friend to load Doodle” continuously .See in the picture below:
2. If the user is online (but in invisible mode), after few seconds (it can take up to one minute, depending on your connection speed), you should get a blank page like in the picture below. So you know that the user is online.





